Casting light on the Necurs shadow

Introduction
The Necurs botnet has a well-known and sordid history of criminal endeavors. Today, it is regarded as one of the most prolific spam and malware distribution botnets in existence. However, despite its reputation for delivering spam, its operators have spent the last couple of years expanding into other malicious activities. Though it is often presented as a monolithic botnet, Necurs is operated like a group of independent botnets sharing a common infrastructure. This fact is relevant for our analysis of DNS traffic to the Necurs domain generation algorithm (DGA) domains and sinkhole data.
A Brief History of Necurs
Since Necurs was discovered in 2012, its operators have periodically diversified their methods of monetizing the network. In 2013, Necurs was a known rootkit that was used to protect the Gameover Zeus banking trojan, making it hard to remove from the infected host[1]. By 2014, law enforcement was able to shutdown Gameover Zeus[2], forcing the operators of Necurs to pivot towards distribution of various ransomware such as CryptoLocker and CryptoWall throughout 2015. CryptoWall operators reaped as much as $235 million from infected victims in the first half 2015[3], with the help of Necurs’ mail distribution.
In 2016, Necurs increased its spamming activity significantly. It was associated with various malware campaigns including the Dridex banking trojan, Shifu, TeslaCrypt, and Locky. By this time the botnet had grown to at least 1 million infected hosts. During 2016, Necurs was observed occasionally disappearing for short time periods, creating corresponding drops in spam. Necurs’ spam volumes that typically would number in the hundreds of millions of messages would quickly fall off for a period before ramping back up again later. This behavior of periods with no botnet activity followed by periods of heightened activity continues to be observed today.
In late 2016, Necurs added a new module that contained both DDoS capabilities and an implementation of a proxy service. To date, CenturyLink’s Black Lotus Labs has not observed the DDoS service being used. However, due to its size, a DDoS attack from this botnet could generate a massive amount of traffic capable of knocking nearly any host offline. In March 2018, Necurs added cryptocurrency mining to its arsenal when it began deploying a module to mine Monero.
Necurs Today
Necurs is now known to contain modules to deliver spam, perform DDoS attacks, proxy illicit traffic, and mine cryptocurrency. This allows the network to be used in a variety of ways to generate revenue for the operators of the botnet. Though there has been a decrease in Necurs’ output, Necurs is still the second most prevalent of spam botnets just behind Gamut, according to the December Mcafee Threat Report[4]. Last year, Necurs was used for spamming stock and cryptocurrency pump and dump schemes, as well as helping lonely individuals find love through dating site spam. Most recently, Necurs has been seen pushing out infostealers and RATs, like AZOrult and FlawedAmmyy, to targeted hosts based on specific information found on infected hosts and deploying a new sophisticated .NET spamming module which can send spam using a victim’s email accounts[5]. These new capabilities represent a significant increase in Necurs’ ability to perpetrate spear phishing, financial crimes and espionage.
From the network perspective, Black Lotus Labs continue to see cycles of botnet inactivity shown by C2 infrastructure going offline and coming back online. At times, they’ve been known to be inactive for weeks. Most recently, the C2s have gone offline for most of the last four months, coming online for short periods of time about once a week.
Necurs Botnet Architecture
The Necurs botnet uses a hybrid architecture which employs a combination of direct C2 communication and peer-to-peer (P2P) communications. While the initial peer list is included in the malware, unlike many P2P networks, new peer lists are distributed directly from a C2, which prevents abusing the P2P protocol to enumerate all bots. Necurs bots periodically contact the C2s to obtain new instructions or configuration information. At each check-in, the C2 will instruct the bot to check back in after some randomized amount of time, usually around 20 minutes. Necurs can provide bots with a list of new C2s to use when bots check in. We’ve observed as many as 22 active C2s at once out of a list of 24, but often only a subset of known C2s are online at any given time. Information about new C2s can also be distributed through DGA domain queries or through P2P communication.
When bots lose connectivity to all known C2s, they begin looking for new ones using the DGA and P2P communication. On the DGA side, each bot generates a list of potential C2 domains and attempts to resolve each domain until it finds a new active C2. A seed value is used to initialize the DGA’s pseudo-random number generator (PRNG) so that it consistently generates the same domain names for the same seed value. This seed value is included in configuration contained within the malware used to infect a host. Depending on the seed used, a bot will query a different set of domains. At the same time, the bot will begin trying to contact known peers to exchange information about the current C2s. Once a new C2 is found, the bot will stop querying DGA domains and contacting peers.
Utilizing the specific DGA seed value included in the malware, along with other related data such as C2 addresses, peer and C2 RSA keys and URL paths, Necurs can manage distinct bot groups independently based on the DGA seed they are using. We’ll refer to these as DGA groups and notate them as follows: If a bot uses a DGA seed of 5, we’ll say it is a member of the DGA5 bot group. Based on which domains a bot is querying, we can infer which DGA group it belongs to. When communicating with a C2, the bot will send an HTTP request to a URL path specific to its DGA group (for example, DGA5 uses ‘/locator.php’) with payload including information about the infected host as well as the DGA seed value, which is encrypted with a key derived from the C2 RSA key. This payload allows the C2 to determine which DGA group the bot belongs to and tailor its response to the bot accordingly.
Necurs has used many different DGA seeds over the years. Currently, DGA5, 9, and 15 are the most active. While Necurs’ architecture supports using different infrastructure for each DGA group, recently, we have observed the same C2 infrastructure and encryption keys being used across all active DGA groups. Necurs uses the encryption keys derived from the RSA keys to encrypt all C2 and peer communications, as well as to check the signature of commands issued by the C2s. If a bot doesn’t have the correct keys, it will be unable to communicate with C2s and peers.
Necurs is modular, allowing different malware modules to be installed to provide additional functionality. The C2 communication channel is used to instruct bots to download and install modules, with new and updated modules being distributed via the current C2 infrastructure rather than separate distribution infrastructure. Black Lotus Labs has witnessed different modules installed on bots in different DGA groups. For example, a Monero cryptomining module was first seen deployed to DGA9. The modular nature of the malware combined with the different DGA groups allows Necurs to test new modules on a subset of bots before deploying them more broadly.
DGA Groups
While DGAs can make it more difficult to disrupt botnets, they can also provide interesting insight into how they are managed. By analyzing the queries for domains associated with Necurs’ DGA, we can better understand how the actors behind Necurs employ different groups of bots and when C2 infrastructure goes offline.
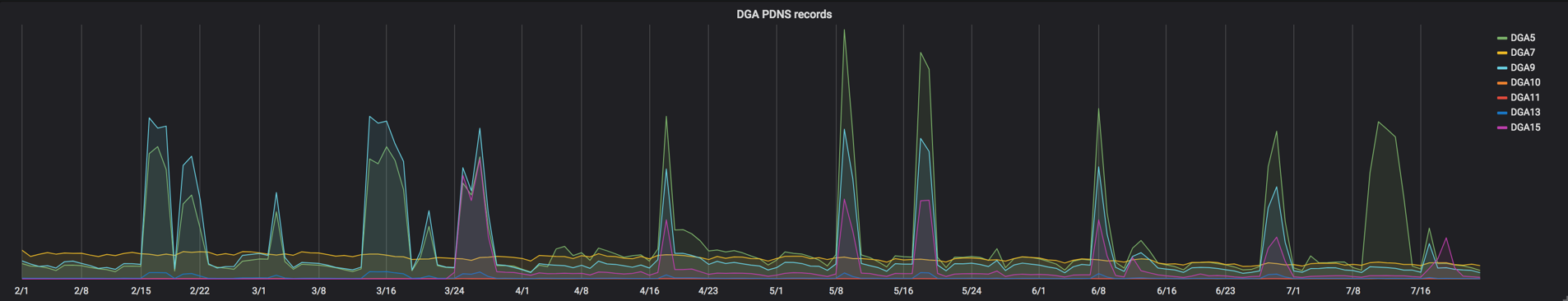
Leveraging our DNS data, we can see the DNS requests made by infected hosts. When a Necurs bot cannot contact any known C2s, it searches for new C2s by querying domains generated by its DGA and querying other bots via its P2P protocol until it finds a new C2. When Necurs’ C2 infrastructure goes offline, we see large increases in Necurs DGA domain queries and bot-to-bot communication as bots attempt to re-establish connectivity, shown below as broad spikes. By tracking queries to these domains, we’re able to see when Necurs’ C2 infrastructure goes dark to some or all of its bots. And because different groups of bots use different DGA seeds, they query different sets of domains, allowing us to fingerprint which groups of bots are affected by the downtime.
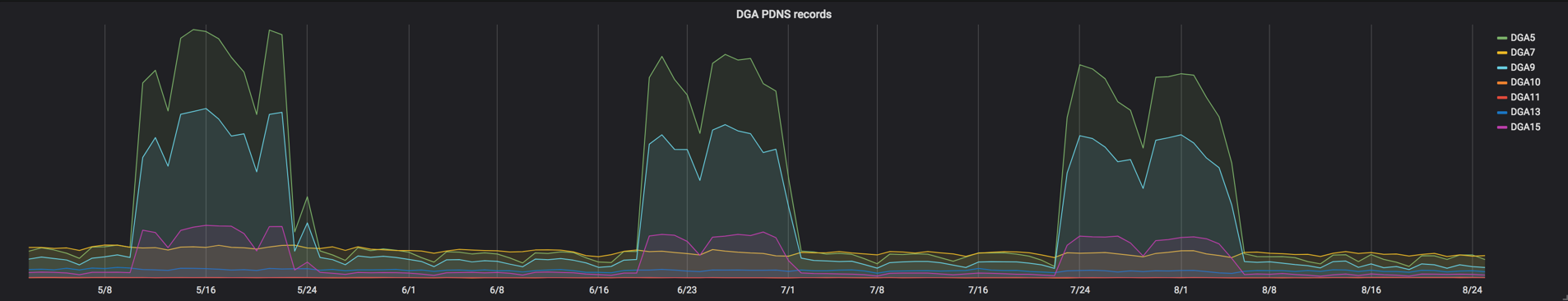
Beginning in May 2018, we observed a trend of regular, sustained downtime for the three most active groups of bots. In the figure below, each spike represents sustained downtime of C2 infrastructure for a large portion of Necurs bots. From May to August, we witnessed a pattern of roughly three weeks on, two weeks off.
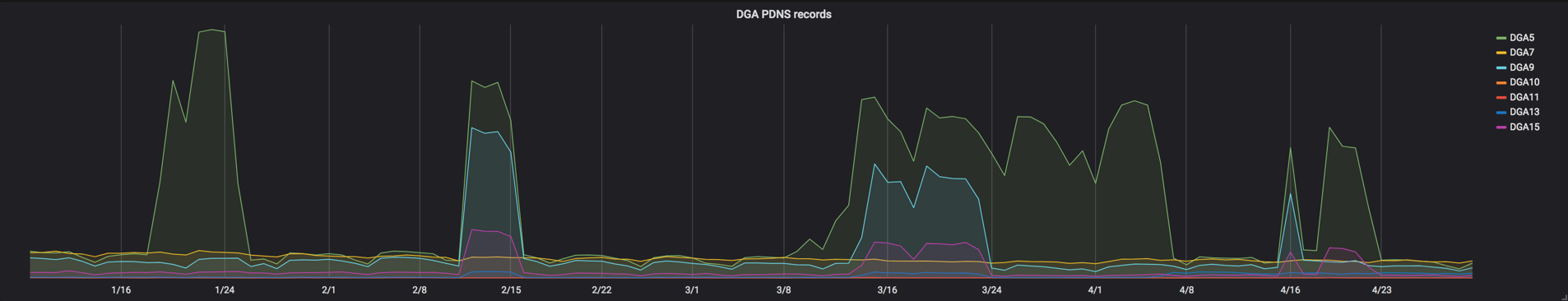
Sometimes Necurs C2s will exclude one or more specific DGA groups, while keeping the lines of communication open with others. Below, we see examples of DGA5 bots (shown in green) being left without C2 communication from early March through early April 2018, while other DGA groups re-established connectivity toward the end of March.
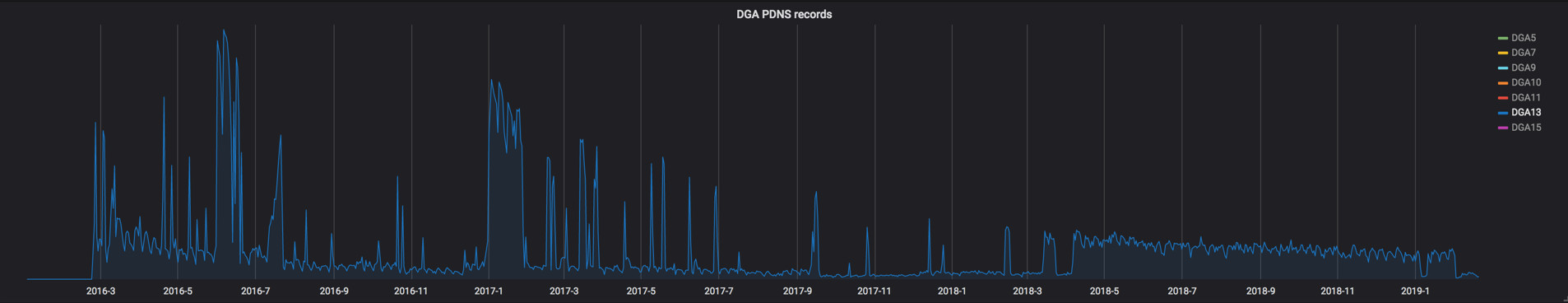
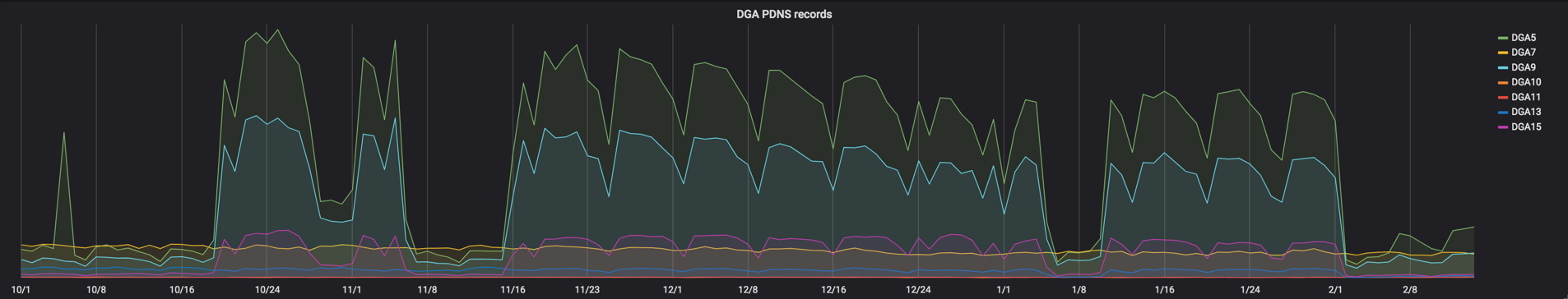
Analyzing DNS data also allows us to recognize when new DGA groups are created. Below we see the birth of the DGA13 group in late February 2016, and around April 2018, we see many DGA13 bots lose connectivity to Necurs for nine months before regaining connectivity.
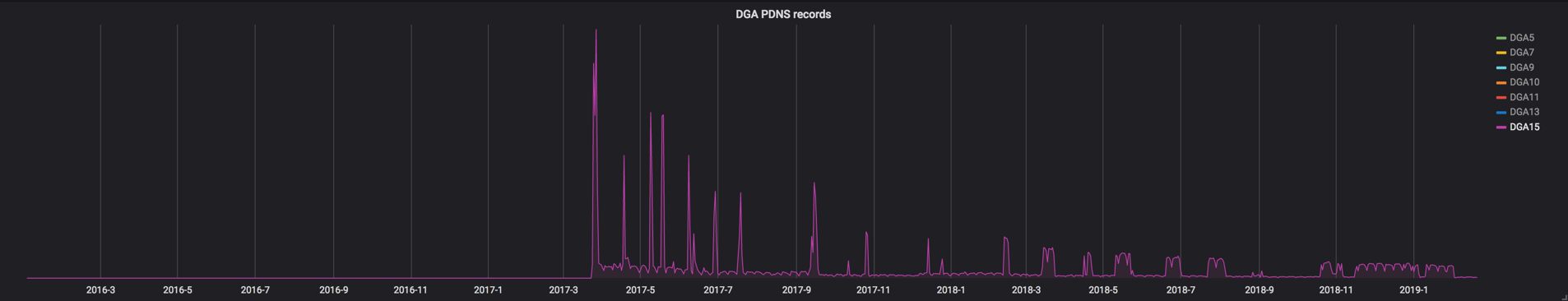
In late March 2017, we see DGA15 make its internet debut.
By tracking each DGA group independently, we can get an idea of the relative size of each DGA group and the changes between them over time. Below, we see DGA9 starting off in the lead only to slowly lose its position to DGA5.
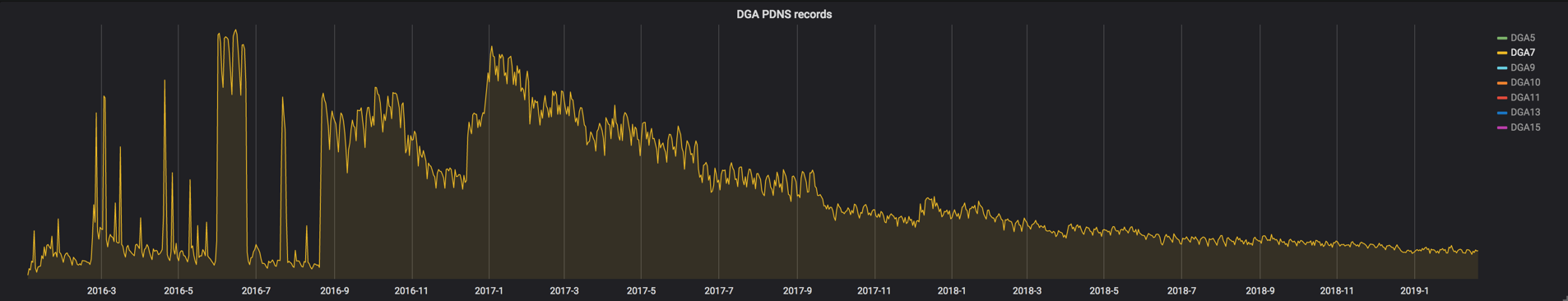
Finally, we can see when DGA groups lose connectivity to C2s indefinitely, like with DGA7. In mid-August 2016, we see many disconnected DGA7 bots, which were never able to reconnect to their C2s.
Beginning in mid-October 2018, we observed the C2s going offline for all DGA groups. It is during these downtimes that we can get the best insight into the size of the entire botnet, as well as the size of each DGA group.
Sinkholes
While DNS data is useful, sinkhole data is even better. A sinkhole, in this context, is infrastructure controlled by researchers or law enforcement that bots believe is legitimate C2 infrastructure. This can happen if the C2’s IP or domain can be commandeered, or in this case, when one its DGA domains is registered. With DNS data, we can only see the DGA domains that are being queried. With sinkhole data, we can see the entire payload the bot sends to what it thinks is the C2. To get this information from the infected hosts they must reach out to the sinkholes being monitored at that time. For many malware families, this is a simple exercise of generating a DGA domain list, registering the domain, and then pointing it to an infrastructure capable of logging. The Necurs authors, however, anticipated this eventuality and implemented a technique to make doing this more difficult.
When the Necurs operators register a DGA domain to inform the bots of the new C2, the domain is not pointed to the real IP address of the new C2 host. Instead, the real IP address of the C2 is obfuscated with what is essentially an encryption algorithm. The bot will then “decrypt” the obfuscated IP address and contact the new C2. This prevents researchers from being able to identify new C2s simply by querying the DGA domains, but more importantly, it makes it difficult for researchers to sinkhole these DGA domains. In order to get the bot to talk to a sinkhole, the obfuscation function must be run against the real IP and the DGA domain’s A record must be set to the resulting value. This can be done by inverting the obfuscation algorithm and implementing it in the same way that the Necurs operators would.
When bots cannot contact any of the C2s they know about, they begin querying all the current DGA domains looking for the new C2. As long as the bot is unable to contact a real Necurs C2, it will go through all 2048 DGA domains for that day, ensuring it will eventually hit one of domains pointing to the sinkhole.
When bots attempt to contact a C2 from a DGA domain, they will send a payload encrypted with a key derived from the current RSA key for that DGA group. By decrypting this payload, it is possible to view the unique ID assigned to every bot. This ID is persistent for each bot instance, and can be used by Necurs operators to identify bots even if the bots’ IP addresses change. This is especially useful for getting a more accurate count of the total number of bots, rather than the total number of unique IP addresses that contact the sinkhole. A bot may hit a sinkhole several times a day, and due to IP churn, it may hit that sinkhole using different IPs. IP churn occurs when a host’s IP address changes, which is common with home or mobile internet connections. When only looking at unique IPs interacting with a sinkhole, IP churn will cause estimates of the total numbers of the bots to be inflated. The opposite is true when multiple bots share the same IP, which can occur if multiple infected devices are behind the same router or firewall NAT.
By analyzing the number of unique bot IDs versus the number of unique IP addresses we see, we can measure how much IP churn affects the botnet size estimate. Over the course of single day, IP churn can cause the number of bots to be overestimated by as much as 25 percent. Over a three-week period, we observed more than 450 percent more unique IP address than unique bot IDs. Over this same period, only nearly 40 percent of bots maintained the same IP address with 20 percent changing IPs nine or more times.
We can more accurately estimate the total number of Necurs bots by looking at unique bot IDs rather than IP addresses. Currently, Black Lotus Labs estimate there are 570,000, though many of these bots have been orphaned and are no longer controlled by the Necurs operators.
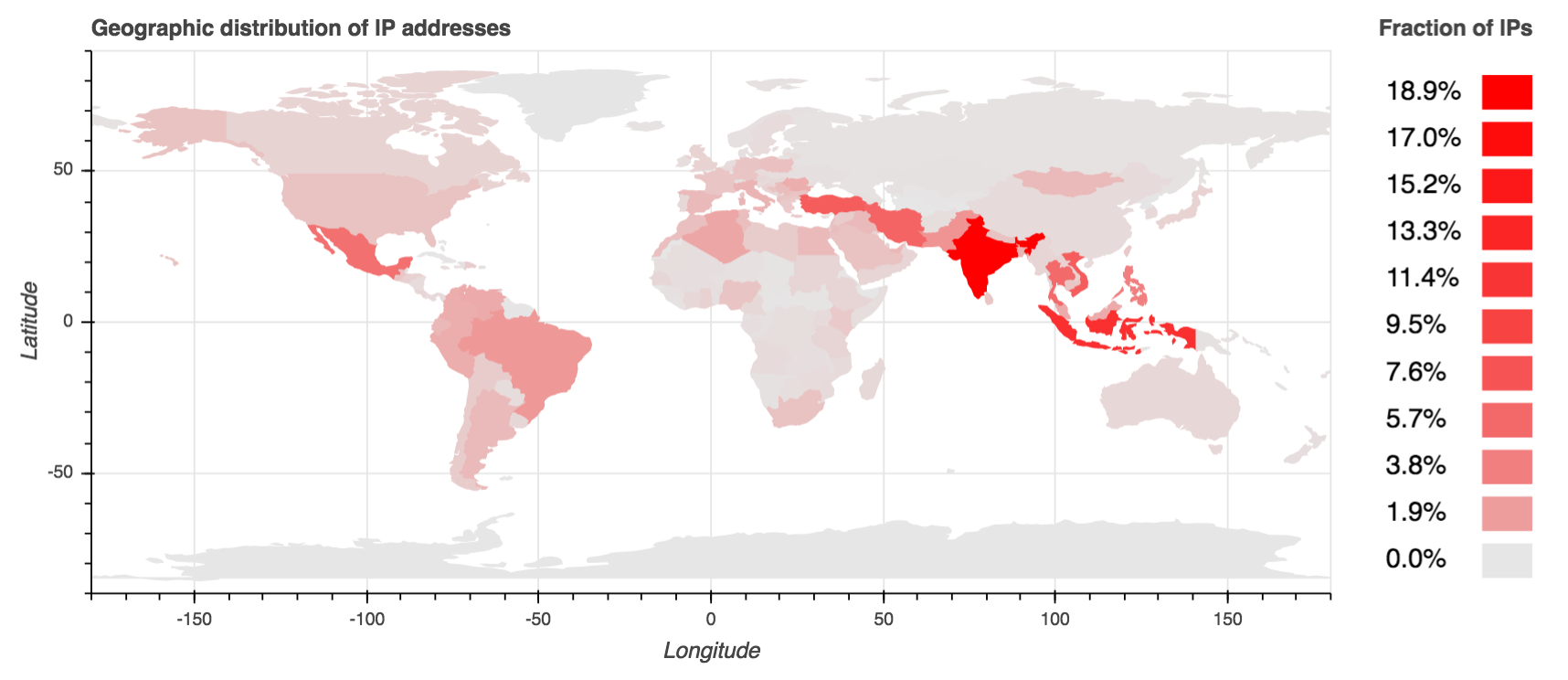
Necurs bots are distributed globally, but about 50 percent of all bots are located within five countries: India, Indonesia, Vietnam, Turkey and Iran. India leads the pack, hosting nearly one in five Necurs bots. There is also a conspicuously low number of bots in Russia. It is widely speculated that the Necurs operators are based out of Russia.
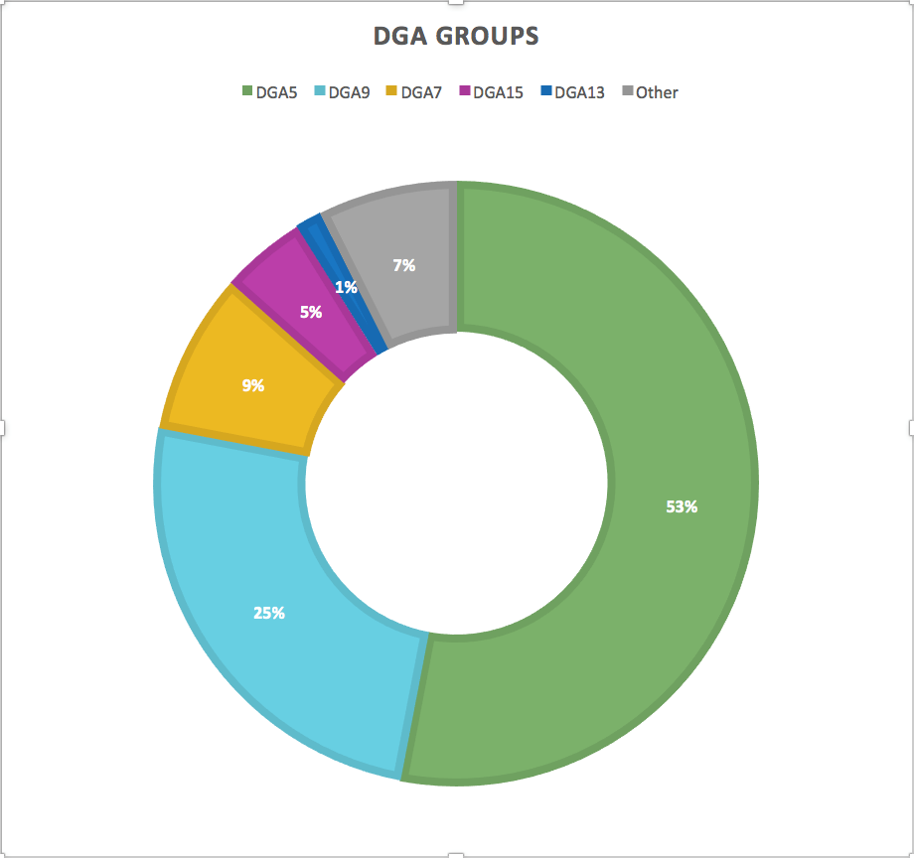
DGA groups
As we’ve observed from DNS data, the DGA groups are different sizes. Using sinkhole data, we can more accurately estimate each group’s population as well as see the differences in their geographic distribution.
Orphans
We observe many bots that are always trying to contact a new C2 by querying DGA domains and attempting to contact known peers, even when the C2s are online. We call these bots orphans. About nine percent of Necurs bots are in DGA7. As mentioned above, this DGA group appears to be defunct. The number of DGA7 bots querying DGA domains and interacting with sinkholes remains relatively constant regardless of whether the C2s are available. While DGA7 represents a significant proportion of orphaned Necurs bots, there is almost an equal number of orphaned bots for other DGA groups. Some of these orphans are for active DGA groups, but for unknown reasons, these bots cannot establish contact with Necurs C2s. This can happen if the bot is using an old key, or an old URL path, and can’t get the updated C2 information for other bots. We have also seen indications that bots can be blacklisted, suggesting Necurs operators can be selective about what bots they want to participate in their malicious campaigns. Other orphaned bots are associated with DGA groups that are no longer active, like DGA10 and 11. In total, we estimate there are currently over 90,000 orphaned Necurs bots. However, orphaned bots aren’t necessarily permanently removed from the botnet. We have recently observed DGA13 bots that had long been inactive regain communication with Necurs C2s.
Conclusion
Despite making it more difficult to takedown the Necurs botnet completely, its use of a DGA is a double-edged sword. Because the DGA domains it will use are known in advance, security researchers can use methods like sinkholing DGA domains and analyzing DNS and network traffic to enumerate its bots and C2 infrastructure, allowing them to mitigate much of the potential damage of this enterprising botnet. CenturyLink has taken steps to mitigate the risk of Necurs to customers, in addition to notifying other network owners of potentially infected devices to help protect the internet. However, the evolution of Necurs’ capabilities and its global distribution make this botnet one the security community will need to continue to watch.
References:
http://www.johannesbader.ch/2015/02/the-dgas-of-necurs/
https://www.cert.pl/en/news/single/necurs-hybrid-spam-botnet/
https://www.mcafee.com/enterprise/en-us/assets/reports/rp-quarterly-threats-dec-2017.pdf
[1] https://www.pcworld.com/article/2103401/gameover-malware-tougher-to-kill-with-new-rootkit-component.html
[2] https://www.fbi.gov/news/stories/gameover-zeus-botnet-disrupted
[3] https://securityintelligence.com/the-necurs-botnet-a-pandoras-box-of-malicious-spam/
[4] https://www.mcafee.com/enterprise/en-us/assets/reports/rp-quarterly-threats-dec-2018.pdf
[5] https://blog.trendmicro.com/trendlabs-security-intelligence/the-new-face-of-necurs-noteworthy-changes-to-necurs-behaviors
![]()