Motivated by their expanding hybrid workforces and an explosion in cloud-based applications, many organizations are seeking a more agile, consistent way to enforce security across their expanding network perimeters that won’t impede network performance and will still provide a seamless […]
Network
Trust: It’s not complicated, just ask my dogs
When I need a break from my busy life, I enjoy long walks with my two English bulldogs. My dogs enjoy them too. Lots of things to sniff, squirrels to chase and not a care in the world as to […]
Your network transformation is just a click away
I ordered something online recently. I’m sure you did too. It’s easy. One click and my items arrived later that day. The experience is designed to make it easier to order the things I need. The order-today-same-day-delivery experience is common […]
The western United States is known for its wide-open spaces and mountains. You can see forever from lots of different vantage points. By geography, the Mountain region in the western U.S. is Lumen’s largest business unit, covering Utah, Idaho, Montana, […]
New infrastructure is helping power business in the southern tech corridor, as the southeast quickly claims space as one of the nation’s top tech hubs. Lumen is helping to accelerate this rise by continuing to invest in the local infrastructure. […]
Fewer customers, more competition: Adapting to a changing FinTech market
If you’re an established fintech company, you have several years of growth behind you, a full book of business and customers completely invested in your service. Congratulations. However, your business environment is changing in at least two critical ways. Venture […]
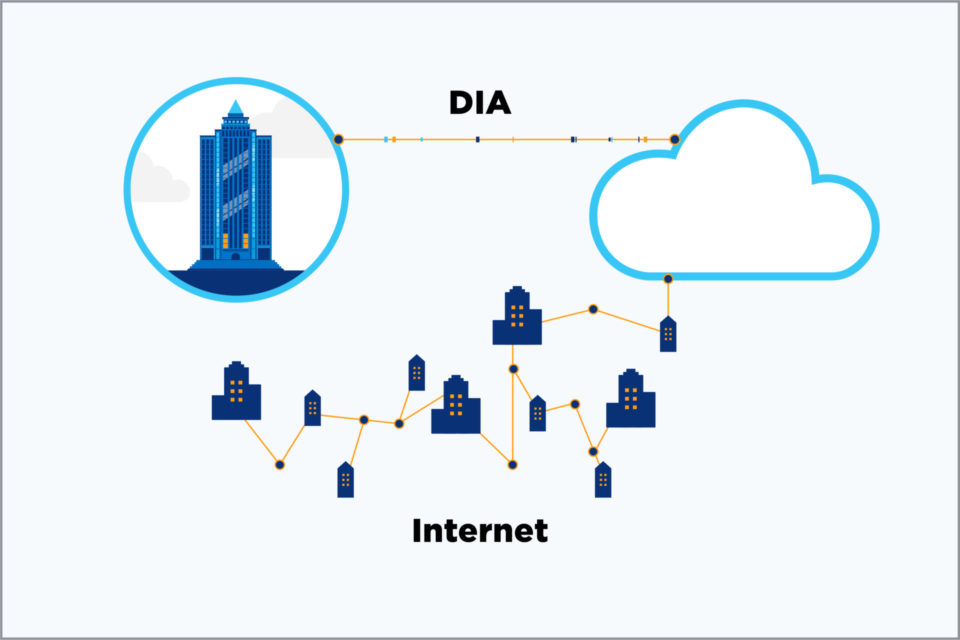
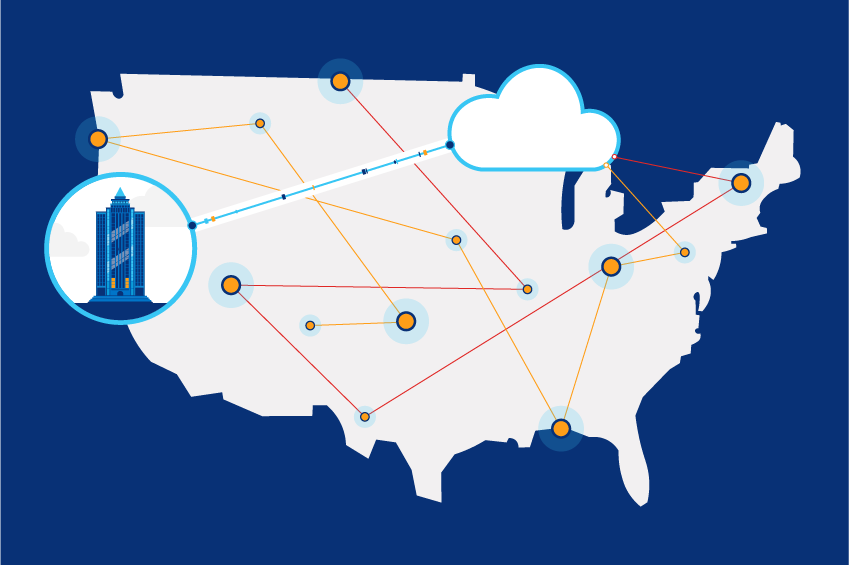
High-speed, low-latency connectivity is vital to enterprise business today. From connecting with your customers to conferencing to accessing your cloud applications, the speed and quality of your internet connection has an important impact on your ability to compete today—and grow […]
Is your business feeling the bandwidth pressure of today’s digital demands? No matter what industry you are in, the answer is likely yes. The surging demands of data-intensive cloud applications like AI and video conferencing, increased eCommerce traffic and hybrid […]
Texas is a big place, and it’s getting bigger as companies move headquarters to the Lone Star state or put major operations here. Local people have a saying: “I wasn’t born in Texas, but I got here as fast as […]
Kicking off your enterprise future
Football season is kicking off and that’s a big reason to celebrate here in Lumen’s Pacific Northwest region. We are long-term technology partners with the Seattle Seahawks. The Seahawks leverage Lumen technology to create an awesome fan experience. I’ll be […]
-
 Lumen is guided by our belief that humanity is at its best when technology advances the way we live and work. With 450,000 route fiber miles serving customers in more than 60 countries, we deliver the fastest, most secure platform for applications and data to help businesses, government and communities deliver amazing experiences.
Lumen is guided by our belief that humanity is at its best when technology advances the way we live and work. With 450,000 route fiber miles serving customers in more than 60 countries, we deliver the fastest, most secure platform for applications and data to help businesses, government and communities deliver amazing experiences.