What is a brute force attack?

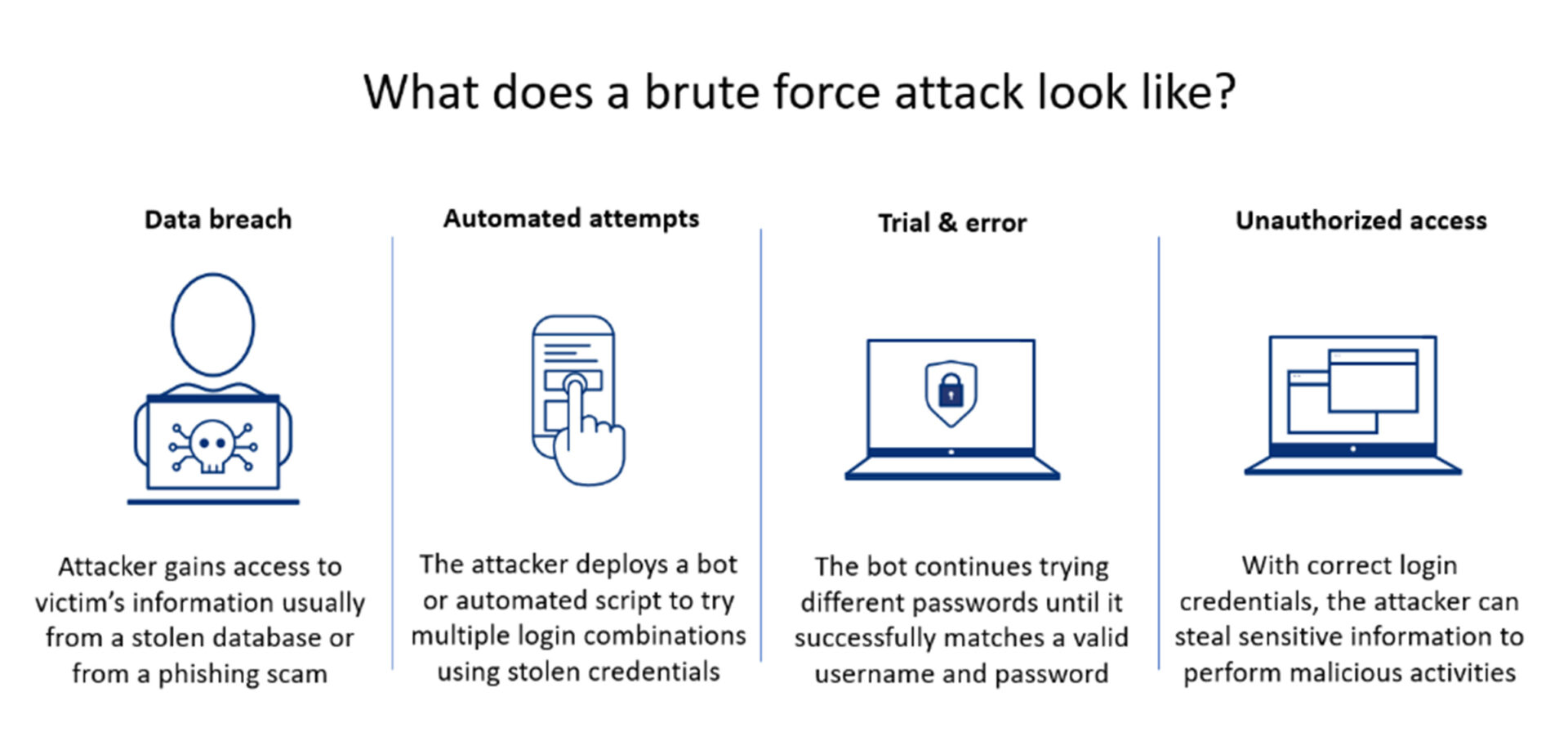
Brute force attacks, used by hackers to gain unauthorized access and compromise networks, pose severe risks to companies’ data security. The process begins by selecting a target and then using automated software to test various combinations of passwords or keys. To break it down, these attacks are like a relentless locksmith trying thousands of keys, hoping to find the one that unlocks your front door. They use trial and error to guess or crack an account password, login credentials, and encryption keys.
The name ‘brute force’ stems from attacks using excessive forceful attempts to gain access to user accounts. A successful breach can result in data theft, loss of revenue, and damage to a company’s brand reputation. As a result, businesses and their employees must prioritize cybersecurity measures to protect themselves from these persistent threats.
Types of brute force attacks
- Simple brute force attacks
A simple brute force attack occurs when an attacker systematically tries all possible combinations or passwords until the correct one is found. For example, an attacker may try to guess a four-digit PIN by starting from 0000 and continuing to increment until they gain unauthorized access to the account.
- Dictionary attacks
A dictionary attack is another password cracking technique in which the attacker selects a target, then tests possible passwords using common words and their simple variations. This method allows hackers to exploit users who choose weak passwords based on easily guessable terms. Hackers also use dictionary attacks for file decryption, attempting to unlock encrypted files by trying various passwords from a dictionary list.
- Hybrid brute force attacks
A hybrid brute force attack occurs when an attacker combines dictionary attack methods with a simple brute force attack. By leveraging both approaches, hybrid brute attacks increase the chance of guessing passwords and bypassing authentication systems.
- Credential stuffing
Credential stuffing attack occurs when hackers leverage stolen username and password combinations to gain access to a victim’s account. Using automated tools, hackers can systematically test these credentials against multiple websites, exploiting users who reuse the same password across multiple platforms.
- Reverse brute force attacks
A reverse brute force attack is a technique where the attacker already possesses a known password typically found through a network breach. Attackers use the password to search for matching login credentials using a list of usernames.
Why do attackers use brute force attacks?
While the motives behind hacker attacks may never be fully known, there are several reasons why a hacker might initiate a brute force attack. These can include:
- Spreading malware
Attackers utilize brute force attacks to spread malware establish control, exploit vulnerabilities, and propagate malicious code to other devices.
- Stealing personal data
Attackers gain access to unauthorized accounts to harvest private information for malicious purposes such as identity theft, financial fraud, and phishing.
- Hijacking systems for malicious activity
When attackers hijack systems to gain unauthorized access, they could install malware, launch further attacks, diminish a company’s reputation, and disrupt business operations.
- Extortion
Attackers use brute force attacks to extort money by gaining unauthorized access to sensitive accounts or data, then threatening to disclose or delete information unless a ransom is paid.
Protect yourself from brute force attacks
There are a few ways to protect yourself from brute force attacks. Using strong and unique passwords of at least eight characters that contain letters, numbers, and symbols to prevent easy guessing. Another way to prevent brute force attacks is by enabling multi-factor authentication (MFA) , a security mechanism requiring multiple forms of identification, which adds an extra layer of security beyond the password itself. 91% of organizations say that password MFA is crucial to combat credential theft and phishing. Another easy precaution to defend yourself from brute force attacks is to keep your software and applications updated with the latest security patches and enable automatic updates to enhance your online security. By regularly updating your software, this helps ensure that any vulnerabilities or weaknesses are patched, making it harder to exploit them.
As a leader within your organization, there are several steps you can take to protect it against brute force attacks. Lumen Application Protection, consisting of web application firewall (WAF) and Bot Risk Management offers a powerful defense against brute force attacks. Lumen WAF and Bot Risk Management act as another line in defense against brute force attacks by identifying and blocking malicious bots attempting to gain unauthorized access, ensuring the security and integrity of your company’s critical data.
To discover how Lumen can effectively shield your business from brute force attacks using Lumen Application Protection, visit our website and schedule a call with a security expert today!
This content is provided for informational purposes only and may require additional research and substantiation by the end user. In addition, the information is provided “as is” without any warranty or condition of any kind, either express or implied. Use of this information is at the end user’s own risk. Lumen does not warrant that the information will meet the end user’s requirements or that the implementation or usage of this information will result in the desired outcome of the end user. All third-party company and product or service names referenced in this article are for identification purposes only and do not imply endorsement or affiliation with Lumen. This document represents Lumen products and offerings as of the date of issue. Services not available everywhere. Lumen may change or cancel products and services or substitute similar products and services at its sole discretion without notice. ©2023 Lumen Technologies. All Rights Reserved.





